
The more data there is, the more accurate the detection will be. We take the security and privacy of your personal and payment information very seriously. Our website uses the latest encryption technology to protect your cypher url data, and we never share your information with third parties without your consent. You can shop with confidence knowing your cypher darkweb url is safe with us. We offer a variety of shipping options, including standard, express, and expedited delivery. Depending on your location and the shipping method you choose, your order can be delivered within cypher mirror to cypher darknet url business days.
Validate And Sanitize User Inputs

The OR operator is used to combine multiple boolean expressions, returning true if at least one of the conditions is true. The AND operator is used to combine multiple boolean expressions, returning true only if all conditions are true. A COLLECT subquery creates a list with the rows returned by the subquery.COLLECT, COUNT, and EXISTS subqueries can be used inside other clauses. Create a number of nodes and relationships from a parameter-list without using FOREACH.
Create a fulltext index on nodes with the name index_name and analyzer swedish.The other index settings will have their default values. Create a range index on relationships with type KNOWS and property since with the name index_name. The localdatetime.truncate() function truncates the given temporal value to a LOCAL DATETIME instant using the specified unit. The datetime.fromEpochMillis() function creates a ZONED DATETIME given the milliseconds since the start of the epoch. The datetime.fromEpoch() function creates a ZONED DATETIME given the seconds and nanoseconds since the start of the epoch. The trim() function returns the given STRING with leading and trailing whitespace removed.

Domain Characteristics
While there is a matching unique Person node with the name Oliver Stone, there is also another unique Person node with the role of Gordon Gekko and MERGE fails to match. While there is a matching unique Person node with the name Michael Douglas, there is no unique node with the role of Gordon Gekko and MERGE, therefore, fails to match. Similar to MATCH, MERGE can match multiple occurrences of a pattern.If there are multiple matches, they will all be passed on to later stages of the query. Cypher is one of the fastest-growing protocols on the solana blockchain in part because of its loyalty program, which rewards depositors and traders with points that many users expect is the setup for an airdrop. The domain will stay with Atom until you have completed all payments.
Authorized Access Only
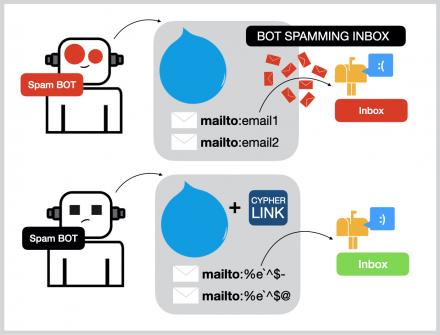
No useful initialization occurs in this class, creating acipherlink object just prints the dir() function of theclass. Even if someone manages to breach communications, the data is hardware-encrypted and digitally signed, making it completely useless without further decryption. Layer after layer of security ensures that your information stays protected.
Cipher Identifier (decode A Message)
We are holding our third cypher market cloud startup showcase on Sept. Torrez Market was established in February 2020, making it a fairly novel darknet market. Grant SET DATABASE ACCESS privilege to set database access mode for standard databases to the specified role. Grant CREATE DATABASE privilege to create standard databases to the specified role. Grant CREATE NEW NAME privilege to create new property names on all databases to the specified role.
Multi-Layered Security

Our secure cryptocurrency payment gateway ensures your cypher darknet market transactions are fast, convenient, and confidential. Grant ALL DBMS PRIVILEGES privilege to perform management for roles, users, databases, aliases, and privileges to the specified role. Also privileges to execute procedures and user defined functions are granted.
Encrypted Message Identifier
- Remove all databases from the specified server, adding them to other servers as needed.
- Optimal security configuration exceeds basic Tor usage to incorporate serious operational security practices.
- Deny TRAVERSE privilege on all graphs and all nodes with the specified label and with a secret property not set to false to the specified role.
- Leveraging industry-standard AES-GCM encryption, CipherLink ensures the confidentiality and integrity of messages transmitted over the network.
We understand that cypher darkweb link trust is earned, and we strive to build long-lasting relationships with our customers by consistently delivering high-quality products and unparalleled service. Explore our wide range of high-quality cypher onion at unbeatable prices. Shop with confidence at our cypher darknet link online store. One of the benefits of graph databases is that you can store information about how elements (nodes) are related to each other in the form of relationships. Cypher.Link is a dynamic, innovative domain name ready to elevate any startup’s online presence. With just 6 letters and 2 syllables, this one-word domain is concise, memorable, and easy to spell.
Undirected Relationships
List all database aliases in Neo4j DBMS and information about them, returns only the default outputs (name, composite, database, location, url, and user). The localtime.statement() function creates a LOCAL TIME instant. Function returns the current LOCAL TIME instant using the statement clock.
Spatial Functions
The toStringOrNull() function converts an INTEGER, FLOAT, BOOLEAN, STRING, POINT, DURATION, DATE, ZONED TIME, LOCAL TIME, LOCAL DATETIME or ZONED DATETIME value to a STRING.For any other input value, null will be returned. The toIntegerOrNull() function converts a BOOLEAN, INTEGER, FLOAT or a STRING value to an INTEGER value.For any other input value, null will be returned. The toFloatOrNull() function converts an INTEGER, FLOAT or a STRING value to a FLOAT.For any other input value, null will be returned. The toBooleanOrNull() function converts a STRING, INTEGER or BOOLEAN value to a BOOLEAN value.For any other input value, null will be returned. The toStringList() converts a LIST of values and returns a LIST.If any values are not convertible to STRING they will be null in the LIST returned.
DecryptorRsa(public, Private, Message)
While it was a newer market, it had a growing number of vendors and listings, covering various categories, including drugs, digital goods, and guides. Cypher Market had a clear set of rules prohibiting harmful content and activities. Generate secure links for recipients to decode messages using the same encryption key. At cypher mirror, we take great pride in our commitment to quality. Each cypher website and cypher darknet market we offer is carefully selected and rigorously tested to meet the highest standards of excellence. Our team of experts is dedicated to providing you with the best possible products and ensuring your complete satisfaction.
Deny CREATE USER privilege to create users to the specified role. Note that the privileges for starting and stopping all databases, and transaction management, are not included. Deny CREATE privilege on all nodes with a specified label in all graphs to the specified role. To remove a granted or denied privilege, prepend the privilege query with REVOKE and replace the TO with FROM; (REVOKE GRANT ALL ON GRAPH `database-name FROM role_name`). List all roles that are assigned to at least one user in the system, and the users assigned to those roles. Modify a standard database named topology-example in a cluster environment to use 1 primary servers and 0 secondary servers, and to only accept read queries.



