
Get unlimited access to the Investment Banking Mastery Program Certification Course Bundle a comprehensive package designed for aspiring investment bankers, finance professionals, and students. Learn financial modeling, valuation, M&A analysis, deal structuring, and more with hands-on case studies and expert-led video lessons. “Many of these forums are owned by people who live outside of the U.S., where American law enforcement cannot put their hands on them,” says Mador, citing Europe, Russia, Latin America, Asia, and Israel as areas where forums have been hosted. Her expertise lies in municipal bond investments, where she provides clear and insightful analysis to help readers understand the complexities of municipal bond markets.
This may involve shutting down the affected systems or even disconnecting them from the network entirely to prevent further damage. Once the source is identified, the team can then assess the extent of the data loss and begin remediation efforts. Stick to cryptocurrency, avoid downloading anything, and don’t share any personal info. In 2019, there were approximately 8,400 active sites on the dark web, selling thousands of products and services daily. But the darkness of these deals doesn’t perfectly hide criminals from accountability.
Dark web monitoring platforms, such as Lunar, provide an automated solution to safeguard personal identifiable information (PII) and credit card details. These platforms continuously scour the deep and dark web, looking for any traces of your sensitive information. By setting up alerts, businesses can receive notifications whenever their PII or credit card information appears in suspicious contexts. This proactive monitoring enables businesses to track and investigate potential threats in real-time, helping to prevent fraud before it can impact their operations.
Student Loan Breach Exposes 25M Records
It has built a reputation for being a reliable source of stolen credit card data and PII. Renowned for its extensive inventory of financial data and sophisticated operating methods, Brian’s Club is a key player in the underground economy of financial cybercrime. A credit card dump refers to a digital copy of stolen credit card information and is commonly used by fraudsters to clone credit cards and make unauthorized purchases. Platforms such as UniCC function as an underground marketplace wherein credit card details stolen from online retailers, banks, and payments companies by injecting malicious skimmers are trafficked in exchange for cryptocurrency.
One Million Credit Cards Leaked In A Cybercrime Forum For Free
Our experts say most people have no idea what’s out there and the information bought and sold can be absolutely devastating to Utah families. The FBI showed us sites on the dark web, one of them listed the items for sale complete with photos, descriptions, guarantees and even seller star ratings. Harris said, “this particular seller has a rating of 4 and a half out of 5 stars. So, it appears they have been doing this for a while and have some good customer service.” The operators of BidenCash have caused significant harm to millions of victims whose personal and financial information has been compromised. The average price of a cloned, physical card is $171, or 5.75 cents per dollar of credit limit.
The Top 6 Deep And Dark Web Credit Card Sites
One of the most popular carding site was Joker Stash, its operators retired in February 2021 and shut down their servers and destroyed the backups. B1ack Stash’s primary motive from the outset has clearly been financial gain, which they have pursued by building a strong reputation as a card seller within the carding community. Our analysis of the payment card details leaked by B1ack over the past six months and the data we’ve collected for the affected local banks indicates that these were largely obtained through phishing campaigns. The data format, which includes user agents and victim IP addresses typically observed in both local and global phishing attacks, allows us to assert with high confidence that it originated from such activities.
Carding Is A Cyber Crime Niche Of Its Own
We will also discuss preventive measures that can be taken to protect against credit card dump attacks. The consequences of a credit card dump can be severe for both consumers and companies. Consumers face financial loss, identity theft, and potential long-term damage to their credit scores.

Hacker Offers To Sell 158 Million Plain-Text PayPal Credentials On Dark Web Forum

Researchers from threat intelligence firm Cyble noticed the leak of the payment-card data during a “routine monitoring of cybercrime and Dark Web marketplaces,” researchers said in a post published over the weekend. The cards were published on an underground card-selling market, AllWorld.Cards, and stolen between 2018 and 2019, according to info posted on the forum. Joker’s Stash was one of the largest and most infamous dark web carding marketplaces, operating from around 2014 until it voluntarily shut down in early 2021.
Historically when darknet sites close down, the operators disappear with customers’ or vendors’ money – this is known as an exit scam. Join us this Halloween for a live webinar exposing real password breaches and how to stop them. It has a bidding feature, with new batches of stolen data being frequently added.
Pour One Out For The Banks That Invested In Musk’s Twitter
By staying informed and following best practices for both personal and business security, we can all help reduce our risk of falling victim to these types of crimes. Hacking involves the criminal gaining unauthorized access to a company’s computer systems that store credit card data. In large-scale attacks, hackers can steal millions of records at once by exploiting vulnerabilities in payment processing networks or third-party service providers.
Community Reactions: Is B1ack’s Stash Legit?
- Routinely reviewing credit card statements for unauthorized or suspicious transactions can help users detect anomalies in expenditure patterns.
- This allows them to create a cloned credit card that can be used to make purchases or withdrawals.
- Our Ultimate Security plans (for US only) protect up to 10 devices with state-of-the-art technologies that predict, prevent and remediate new and existing cyber threats whether you’re at home or on the go.
- The illegal carding market, which can be accessed through the dark web, went live during June, 2022.
- The allure of easy money is not worth the potential fines, imprisonment, and ruined reputation that can result from participating in such illegal activities.
Given the platform’s history of providing genuine data in previous releases, it seems improbable that the shop would risk tarnishing its reputation with a fake pack. However, it’s noteworthy that this recent release lacks the comprehensive data quality that previously set BidenCash apart. Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data. “When vDOS got breached, that basically reopened cases that were cold because the leak of the vDOS database supplied the final piece of evidence needed,” she said.
- They can then sell the account credentials to a buyer who can log in and drains the funds, or the vendor can transfer the requested amount of money from the victim’s account to the buyer’s account.
- Pattern recognition through machine learning has revolutionized how we spot compromised cards.
- A significant portion of this data was uniquely identified in our intel collection.
- Sellers often provide buyers with validity rates for their data and even offer replacements for cards that don’t work.
- The consequences for consumers can include financial losses due to fraudulent purchases and identity theft.
With features like real-time alerts, data breach monitoring, and comprehensive dark web post monitoring, Lunar helps organizations stay ahead of deep and dark web threats in an increasingly hostile digital environment. In addition to just selling credit card details, some threat actors offer a “complete package” often referred to as “Fullz”. Fullz includes full personal details as well as financial details such as bank account details or social security numbers, which can be used for a full account takeover or identity theft. The supply chain for carding stores like Joker relies on large data breaches, usually sourced from hacks involving point-of-sale software for large retail or merchandise outlets. Buyers, also known as “carders,” typically will then turn around and use the data to clone a card or multiple cards, which can then be used to make illegal bulk online purchases that can be re-sold for a net profit. Threat actors have leaked 1 million stolen credit cards for free online as a way to promote a fairly new and increasingly popular cybercriminal site dedicated to…selling payment-card credentials.
Tentacles Of ‘0ktapus’ Threat Group Victimize 130 Firms
Alongside the trade of credit card data on the dark web, complimentary tools named checkers are often offered and sold on the dark web. Checkers are tools used by individuals and organizations to verify the validity and authenticity of credit card information and are used by threat actors to check the illicit information they purchase. While Joker may be stepping down, the site’s demise is expected to have a net-zero effect on the criminal enterprise that undergirded it, reports Gemini Advisors, one of the threat research groups that originally reported its closure. This is because resellers of stolen card data are likely to pivot to other large-scale dump forums. The underground payment card economy is “likely to remain largely unaffected by this shutdown,” researchers write. According to a blog by SOCRadar, the release of such comprehensive data poses significant risks, including financial fraud and identity theft.
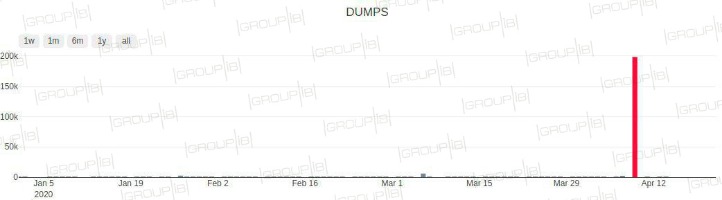
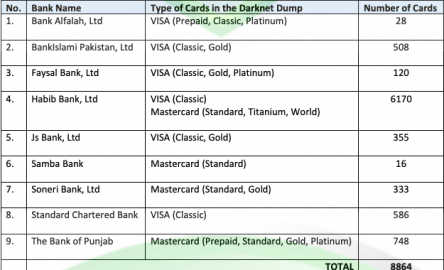
Cyberint conducted an in-depth analysis of a subset of the leaked payment card data involving six major local banks, totaling 45,195 cards. Our analysis showed that 42,310 of these stolen cards were unique or first observed in the Argos intel collection. This category, known as Dumps on the dark web, encompasses the raw magnetic strip data of credit cards.



