
The dark web is a part of the internet that is not indexed by traditional search engines. It requires specific software, configurations, or authorization to access. Most commonly, users rely on the Tor browser to navigate these hidden sites.
According to the United States Attorney’s Office, the ring of thieves obtained the credit card information on the dark web, and used that information to create their own cards. The fraudulent credit cards were used to purchase gift cards, flights, hotels stays, and other goods and services. The dark web—about 6 percent of the internet—is home to TOR-encrypted sites and many illegal activities. Cybercriminals buy, sell, and trade corporate data, PII, and other digital assets here, according to IntSights, a security provider. Threat actors sift through massive data dumps looking for credit card numbers, email addresses, login credentials, and more. But fewer than 1 percent of internet users have actually visited the dark web, according to IntSights.
Taking Back Control: Protecting Your Business
- Indeed, Quebec accounts for about 22.46% of the total Canadian population.
- Malware—malicious software—infects a user’s computer, phone, or device to secretly record keystrokes, steal stored information, or redirect online transactions.
- In fact, the overwhelming majority of leaked credit cards in past months originate from Telegram channels.
- Even highly secure financial institutions and payment processors are vulnerable to data breaches.
If you’ve ever wondered where your stolen credit card turns up, a cybersecurity firm is offering hard proof. If you suspect your credit card information has been stolen, immediately contact your bank, monitor your accounts for unauthorized transactions, and consider placing a fraud alert on your credit report. We’ll cover how they work, the risks involved, and the steps to stay safe if you’re tempted to venture into this hidden world. Whether you’re looking to protect your information or simply satisfy your curiosity, we’ve got you covered.
Brief Bio: Russian Market
A quick guide for developers to automate mergers and acquisitions reports with Python and AI. If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API. These details are needed for physical use such as withdrawing money from ATMs.
The use of such platforms is crucial for maintaining the integrity and security of customer data, and it provides an additional layer of defense against cybercriminal activities. The dark web is often portrayed as a shadowy realm of illicit activities, and one of the most notorious aspects of this hidden internet is the trade in stolen credit cards. This article delves into how dark web credit cards operate, the risks involved, and what you need to know to protect yourself. While an average person may or may not know anything about dark web, chances are that their sensitive details including credit, debit card data may have ended up there. Hackers and financial scamsters sell stolen credit card details with markets and forums on dark web and make millions out of the illegal trade.
Emily In Paris Star Lily Collins ‘painfully’ Slim Look SHOCKS Internet; Know About Her Past Eating Disorder
Vietnam came in second on the count of compromised accounts, with 322 corporate account cracks. Cyble Inc.’s mission is to provide organizations with a real-time view of their supply chain cyber threats and risks. Their SaaS-based solution powered by machine learning and human analysis provides organizations’ insights to cyber threats introduced by suppliers and enables them to respond to them faster and more efficiently.
Collecting Threat Intelligence
Hackers can use what’s called a “man-in-the-middle” (MITM) attack to intercept your connection and collect any data you share, including credit card information. If you throw away a pre-approved card, accidentally toss a replacement card, or forget to shred your statements, anyone can take them out of the trash and use them. Learn the top ways scammers get access to your credit card and how you can protect it. It would help if you considered choosing a VPN with a no-logs policy and a high-level encryption protocol to avoid online credit card theft.
Beyond Free Antivirus: 5 Reasons Smart Consumers Choose Full-Strength Protection For Their Devices

Cybercriminals are likely more prevalent in countries that are struggling financially. Those who live in poverty are more likely to resort to illegal methods to make money, such as cybercrime. Stealing credit card information and selling it can prove to be lucrative for the individuals behind it, with such sensitive data usually being sold in batches. After all, cybercriminals can use the cards to buy items, extract the cash from the account, or just continue to charge the card itself until the bank realizes that the transactions are fraudulent. The endgame for cybercriminals is peddling stolen credit cards that go for an average rate of $10 to $20 per card on the dark web, according to Mr Foss.
Why Are They Sold?
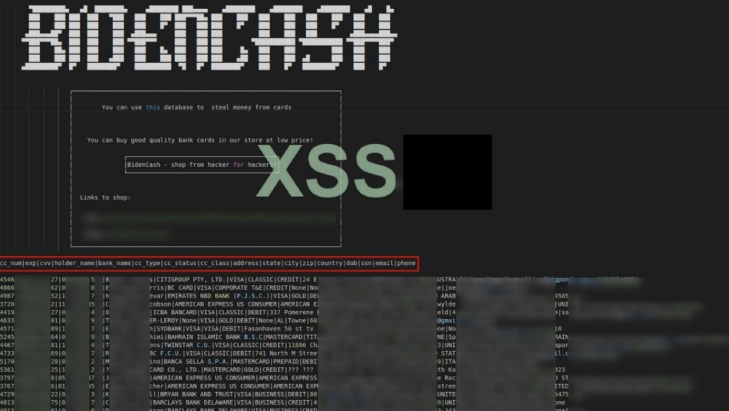
– Read feedback from experienced Dark Web users or trusted individuals who have had successful transactions with the vendor. While many are illegal, some transactions could involve legal goods and services, but caution is advised. Most users on the Dark Web are logged into a Virtual Private Network (VPN) to further conceal themselves. Another forum member with a low reputation score refers to the free cards as “dead,” apparently suspecting that the leaked data is not fresh. A member with an average reputation concurs, positing that the cards were “dead” before they were released.
These illegal activities are made possible by the layer of anonymity provided by Tor and other similar networks. If you receive an alert that your information has been compromised, it’s worth changing your sign-in information as quickly as possible. Still, because users are anonymous, the dark web is also used as an online black market by criminals for illegal activities like selling stolen information.
A quick check with your favorite online retailer will show that a GE Profile Dryer goes for $989, a 10-pack of Play-Doh can be had for $7.99, and a loaf of Pepperidge Farm Farmhouse Hearty White Sliced Bread is $3.59. Eliminate active threats with 24/7 threat detection, investigation, and response. “I always celebrate anybody who perhaps realises that they’re in an occupation, which is criminalised and decided not to enhance that further,” says Alex Hudson, the National Crime Agency’s head of darknet intelligence. For police, who would prefer criminals to face justice, this kind of exit causes mixed feelings.

Once obtained, these stolen credit cards are quickly sold on the dark web, where they can be used for fraudulent transactions or identity theft. Protecting your credit card information is crucial to avoid financial loss and potential legal troubles. By regularly monitoring your credit, using secure payment methods, and being cautious online, you can minimize the risk of your credit card falling into the wrong hands. In the dark underbelly of the web, cybercriminals employ various sophisticated methods to exploit credit cards for illicit gains. One common technique involves acquiring stolen credit card data from online marketplaces on the dark web. These underground platforms facilitate anonymous transactions where criminals can purchase credit card information in bulk, complete with the cardholder’s name, number, and CVV.
Challenges In Combating Dark Web Credit Card Fraud

Darknet markets — also known as cryptomarkets — provide a largely anonymous platform for trading in a range of illicit goods and services. Accessing the dark web can only be done using specific browsers, such as TOR Browser. Trustwave, A LevelBlue Company, is a globally recognized cybersecurity leader that reduces cyber risk and fortifies organizations against disruptive and damaging cyber threats. Our comprehensive offensive and defensive cybersecurity portfolio detects what others cannot, responds with greater speed and effectiveness, optimizes client investment, and improves security resilience. As we have seen, Dark Web pricing reflects a combination of database security weaknesses, demand for specific data types, and the effectiveness of fraud detection systems worldwide. As cybersecurity improves in certain areas, the market adapts, creating variable pricing across regions and data types.



