
The number of market-U2U and market-only buyers also drops as a consequence of operation Bayonet. However, compared to sellers, the drop is notably smaller, and the number of buyers rapidly recovers to previous values. Moreover, the number of multibuyers increases, which suggests a fast response from buyers to external shocks by trying to diversify their sources. Its presence significantly escalates the likelihood of a darknet market attracting law enforcement attention, he said, because fighting the drug is a priority for international law enforcement. Once you download and launch it, it will connect you to the TOR network and you’re good to go. You can use TOR to surf the pedestrian web (the everyday Internet you and I know and love) anonymously, or you can use it to access the Darknet.
Types Of Bitcoins Accepted

In 2025, the darknet continues to provide a secure platform for the exchange of goods, with drug trade being one of its most prominent sectors. The best darknet markets have evolved to prioritize user safety, transaction efficiency, and product quality. These platforms rely on advanced encryption and decentralized systems to ensure anonymity and reliability for both buyers and sellers. Overall, our study provides a first step towards a better microscopic characterisation of the DWM ecosystem, indicating a direction of investigation that may be of interest to both researchers and law enforcement agencies. The results further support the recent efforts of law enforcement agencies to focus on individual sellers43,44,45, as well as, more recently, also buyers46,47.
It is considered a go-to site for malware purchasing, providing keyloggers, trojans, and other Malware as a Service products. STYX Market focuses specifically on financial fraud, making it a go-to destination for cybercriminals engaged in this activity. Tune in as CoinDesk runs down daily action in bitcoin markets and some of the most important recent industry development. Note that just because a site or service is running on an encrypted, hidden network does not necessarily mean that it is illegal or dubious.
Specialized Marketplaces
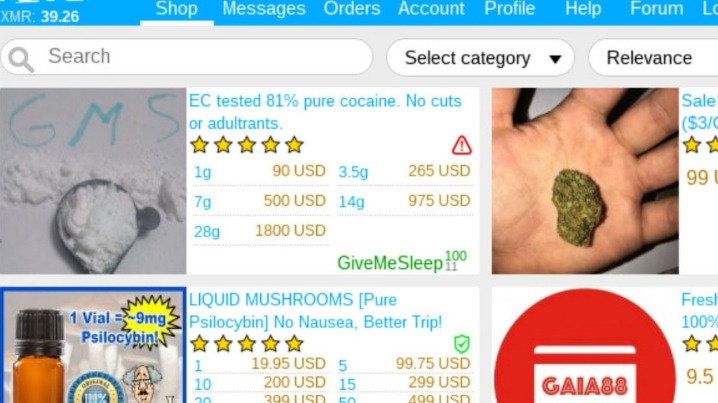
It offers counterfeit documents, financial fraud tools, hacking and malware services. It has an active forum and community along with an extensive user vetting process. Some dark web marketplaces even host content that’s not just illegal but extremely harmful, so it’s really important to understand the risks before diving in. Others are looking for stolen data, hacking services, or even banned books and political content. By supplying stolen data, these dark web links fuel many online scams and identity theft operations, playing a critical role in the darker aspects of the internet. Freshtools is a unique marketplace in that it does not only provide the stolen data, but it allows criminals to purchase MaaS which can cause further damage to the victims.
Fifth, we consider the lifetime of each entity i at time t, defined as the time interval between the first and the last transaction performed by the entity until time t, denoted by \(\ell _i(t)\). This feature is satisfied when \(\ell _i(t) \ge L\), where L is the fixed value of minimum lifetime. From 2012 to 2016, the largest component of S2S network continuously grows in number of nodes and connections, as shown in Fig. Then, during 2017 and 2018, it shows the structural change due to operation Bayonet, when it shrinks. However, unlike the multiseller network, the S2S network recovers during 2019 and 2020, but slower than the multibuyer network recovery.
Darknet markets are increasingly relying on bitcoin (BTC) as their cryptocurrency of choice. This change comes in the wake of major exchanges delisting privacy tokens like monero (XMR), which has forced users purchasing illicit goods to pivot back to bitcoin for better liquidity and broader accessibility. The darknet is a part of the Internet that is not accessible via traditional search engines. To access it, you need special software such as Tor, which makes it possible to surf anonymously.
Torzon Market
Market takedowns create temporary disruptions, but they rarely dismantle entire networks. Sophisticated players shift operations, adopt new aliases, and resume business within weeks. Cryptocurrencies have replaced fiat currencies as the default medium of exchange on the dark web. Bitcoin continues to lead as the most widely accepted digital currency due to its high liquidity and global acceptance. However, its transparent blockchain has prompted users to shift toward more private alternatives. Given the explosive growth of these markets, organizations must prioritize proactive threat monitoring.
Silk Road Was The Darknet Market Testing Ground For Bitcoin
It features over 40,000 listings including narcotics, counterfeit items, hacking tools, and stolen data. The marketplace is well-known for its bug bounty programs and robust security mechanisms, including mandatory 2FA. Generally, while most darknet markets accept standard bitcoin (BTC), others may accept alternative cryptocurrencies depending on the platform. It, however, becomes illegal when you use it for unlawful activities such as buying drugs, weapons, stolen data, or engaging in cybercrime. Many people, including journalists and researchers, access the dark web legally for work-related purposes. Prior to 2015, bitcoin used to hold most of the market share in darknet markets, followed only by fiat currency.
These platforms leverage advanced encryption technologies and decentralized systems to ensure that transactions remain private and secure. The use of onion addresses and Tor networks further enhances user privacy, making it nearly impossible for third parties to trace activities. The marketplaces are also a hotbed for cyberattacks, and the threat of law enforcement means they could be shut down at any time. The Silk Road market operated on the Tor network, which masks your identity through IP address anonymity and encryption technology, while allowing you to find other websites on the dark web. Within the Tor network, customers could access the Silk Road, then anonymously connect with vendors to buy illegal goods with cryptocurrency. We showed that a small fraction of traders is responsible for a large fraction of the trading volume, and by analysing the networks of buyers and sellers, we found different resilience regimes.
Popularity And Market Demand:
Launched in 2020, Cypher Marketplace sells fraudulent documents, stolen credit cards, fake IDs, and malware. Its emphasis on user anonymity and document forgery makes it a core tool for identity fraud. Launched after the takedown of AlphaBay in 2021, Abacus Market has rapidly risen to prominence.

The number of actors in the ecosystem is affected by several factors, especially market closures. Notably, the number of buyers and sellers significantly drops after the operation Bayonet in the last quarter of 2017, which shut down AlphaBay and Hansa markets, causing a major shock in the ecosystem34. However, the number of buyers rapidly recovers, which does not happen to sellers. The Nucleus Marketplace was a reasonably successful criminal sales forum operating on the dark web between 2014 and 2016. In that time it sold everything from drugs, the primary source of its income it would appear, to fake IDs and computer hacking services. All of that came to an abrupt halt in 2016 when the dark web site, well, went dark.
Early Warning Signals For Predicting Cryptomarket Vendor Success Using Dark Net Forum Networks
This ensures that both buyers and vendors can operate without fear of exposure. Amidst this chaos, Alphabay emerged as the premier darknet marketplace before law enforcement intervened. In order to investigate the role of direct transactions between market participants, we now analyse the evolution of the S2S network, i.e., the network of the U2U transactions involving only sellers. The nodes of the S2S network are active sellers (i.e., sellers that are trading at the time) and two sellers are connected by an edge if at least one transaction was made between them during the considered snapshot period. Cybersecurity companies and researchers monitoring darknet markets face legal and ethical restrictions. Legally, they are limited to observing publicly accessible areas using tools like the Tor browser, without engaging in unauthorized access or illegal transactions.
- At KELA, we help you identify and mitigate risks by providing actionable intelligence from the darknet.
- These platforms rely on advanced encryption and decentralized infrastructure, making them highly resistant to external interference.
- We’ve also included tips for keeping your connection and data safe when visiting the dark web.
- Merchants, especially in environments such as darknet markets are looking for simplicity, something that Lightning doesn’t currently provide.
- Despite advancements in blockchain analytics and regulatory measures, privacy-focused technologies continue to pose challenges for oversight and Anti-Money Laundering (AML) enforcement.
- Efficient navigation is facilitated by darknet market lists and onion URLs, which are regularly updated to ensure accessibility.
Swiss Bank Sygnum Launches BTC Alpha Fund, To Grow Bitcoin 8–10% Annually
The multihomers play a crucial role in the ecosystem because they act as edges between markets. Hence we do not distinguish multisellers by the number of markets in which they operate. Just like eCommerce stores on the regular web, darknet marketplaces come and go and rise in fall in popularity. Currently, and from my perspective, Empire is the most popular darknet market but is frequently offline for periods, making it hard to access. White House Market is another popular market but requires you to use Monero instead of Bitcoin. To find out which darknet markets are currently popular, see Darknetlive.com or dark.fail.
Jacob Riggs is a senior cyber security professional based in the UK with over a decade of experience working to improve the cyber security of various private, public, and third sector organisations. His contributions focus on expanding encryption tools, promoting crypto-anarchist philosophy, and pioneering projects centred on leveraging cryptography to protect the privacy and political freedoms of others. The Tor network provides strong anonymity, making tracking difficult, but it’s not perfect. That’s why it’s best to always take additional privacy measures, such as using a VPN, and follow safe browsing practices. ⚠️ Unfortunately, once your data appears on the dark web, there’s no reliable way to erase it.
Whether the result of fear, greed, or a secret takedown, the outcome is the same. Users are left empty-handed, and another major darknet chapter ends… in silence. Although the site’s administrator, Vito, attributed the problems to DDoS attacks and a spike in traffic, TRM Labs observed that this pattern closely resembles known exit scams.
Even as the focus on darknet market activities intensifies, industry experts stress that illicit transactions account for only a small fraction of overall crypto activity. Jardine clarifies that such transactions typically remain at or below 1% of total crypto exchanges. Chainalysis data further supports that approximately 0.14% of all crypto transactions, or around $50 billion, are linked to illicit practices. Moreover, the rise of stablecoins as an illicit payment mechanism has prompted countermeasures from blockchain stakeholders. For example, the Tron-led T3 Financial Crime Unit—comprising partners like Tether and TRM Labs—recently froze over $100 million in funds suspected of being involved in illegal activities.



