
TRM Labs reports that both its clearnet mirror and hidden-service infrastructure became inaccessible, and the site’s operator, known only as “Vito,” vanished along with users’ escrowed funds. 2easy has quickly gained traction as a go-to platform for hackers looking to buy and sell databases containing breached credentials, Social Security numbers, financial records, and login details for online banking and e-commerce platforms. Fresh Tools Market has become a go-to platform for cybercriminals seeking access to malicious software such as keyloggers, Remote Access Trojans (RATs), and ransomware-as-a-service. These features help establish trust between buyers and sellers, providing users with a sense of security that many other markets lack.
Strategic AI In Cyber Defense: How To Stay Ahead Without Increasing Risk
A year from now, these totals will be higher, as we identify more illicit addresses and incorporate their historic activity into our estimates. For instance, when we published last year’s Crypto Crime Report, we reported $24.2 billion for 2023. Much of that growth came from various types of illicit actor organizations, such as vendors operating through Huione, which provide on-chain infrastructure and laundering services for high-risk and illicit actors. A concerning new trend is for hacked debit card data for high-balance accounts to be bundled with SIM cards and cryptocurrency accounts. These all-in-one fraud packages permit scammers to SIM-jack the account 12 and drain the funds into the intermediary crypto account, where the stolen cash is easily laundered.

The market is known for its large selection of products, including drugs, digital goods, and services. Dark0de Reborn uses a multi-signature wallet system to ensure the security of its users’ funds, and it accepts Bitcoin, Litecoin, and Monero as payment methods. The stolen data supply chain begins with producers—hackers who exploit vulnerable systems and steal sensitive information such as credit card numbers, bank account information, and Social Security numbers. Next, the stolen data is advertised by wholesalers and distributors who sell the data. Finally, the data is purchased by consumers who use it to commit various forms of fraud, including fraudulent credit card transactions, identity theft, and phishing attacks. Written by Flashpoint’s Intelligence Team, this report is also supported by research from blockchain intelligence firm TRM Labs.
Global Crackdowns Leave Crypto Criminals Few Options
Due to the concerted law enforcement action (and successive sanctions) against Hydra, cryptocurrency cash-out services are often wary of running under the same name as they did on the now-defunct market. Thus Flashpoint analysts have observed several cash-out services and their users stating that the service in question had been present on Hydra, typically in a positive context. The takedown of Hydra market undoubtedly caused a major rupture in the Russian darknet market ecosystem. In its wake, the US has also sanctioned several mixers and risky exchanges that handled stolen funds and which had exposure to Hydra wallets. Major drug markets in the Dark Web are now worth around $315 million annually according to the United Nations Office on Drugs and Crime (UNODC). As encryption, anonymity and privacy are central to the design of the darknet and its various drug markets, up-to-date information on drug trends is difficult to come by.
Twenty One Capital CEO Sees 200X Bitcoin Boom As Fed Rate Cut Pushes BTC Beyond $117K

Of the surveyed countries, Germany (65%), India (58%), and the United States (55%) had the smallest share of people unfamiliar with the Dark Web. Watch our cyber team share their key insights from their investigations into the biggest dark web trends in 2022. Established in 2022, WizardShop is one of the biggest data stores on the dark web, focusing mainly on carding and financial data.

Down Goes Hydra
In light of recent busts, however, dark web operators have increased their vigilance and are scrutinizing applicants more thoroughly. These days, you often have to pass stringent verification and vetting processes to join a forum. Admins may require references from other members or verification tokens from other trusted forums. Some forums and dark web marketplaces now require a substantial cryptocurrency down payment to even get access to their services.
Dark Web Trends
Additionally, Tor enables users to access darknet sites hosted on .onion domains, something most common browsers can’t do. Freshtools was established in 2019 and offers various stolen credentials, accounts, and host protocols like RDP. It is considered a go-to site for malware purchasing, providing keyloggers, trojans, and other Malware as a Service products. Torzon Market has established itself as a significant player in the darknet ecosystem, offering a secure, user-centric platform for anonymous trading. Its commitment to privacy, diverse product offerings, and robust security measures make it a preferred choice for users seeking discreet transactions within the darknet.
Dark Web Illegal Activities Stats
Operation Bayonet, which would ultimately lead to the shutdown of several prominent marketplaces, began with Dutch police seizing another lesser-known market called Hansa Market. After compromising Hansa, authorities secretly operated the market for almost a month. Attorney’s Office for the Eastern District of California filed a civil forfeiture complaint against Alexandre Cazes and his wife’s assets located throughout the world, including in Thailand, Cyprus, Lichtenstein, and Antigua & Barbuda. One of the central76 discussion forums was Reddit’s /r/DarkNetMarkets/,777879 which has been the subject of legal investigation, as well as the Tor-based discussion forum, The Hub.

Several alternatives remain for those looking to continue their business in 2024 with marketplaces like Bohemia, Archetype, Darkmatter, Incognito and many others happily taking the influx of both customers and vendors affected by closures. For those interested in digital products – like stealer logs – RussianMarket and 2Easy are the most popular alternatives to Genesis, having already proved their capabilities. The dark web, accessible only through special software like Tor, constitutes a small fraction of the deep web and hosts a substantial share of illegal activity.
- Silk Road was eventually shut down by the FBI in October 2013, following the arrest of Ross Ulbricht.
- Vendors on Incognito paid a registration fee and a 5% commission on every sale.
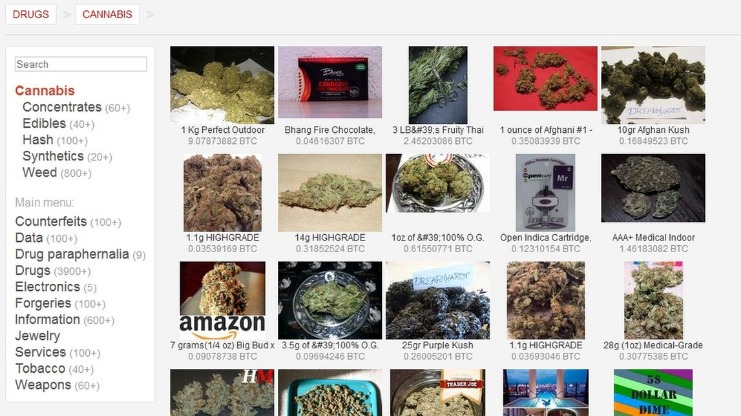
- For those seeking specialized products, Cannabis Road and Berlusconi Market cater to niche audiences, offering a curated selection of items.
- Since the summer of 2022, the aforementioned markets have waged war against each other, involving the spreading of rumors, the doxing of administrators and staff members, distributed denial of service attacks and breaches.
This information is then processed to generate an index of average prices for a broad range of specific products. During the second half of 2022, law enforcement cracked down on a large number of darknet markets, temporarily disrupting the supply of such illicit goods. Some dark web marketplaces even host content that’s not just illegal but extremely harmful, so it’s really important to understand the risks before diving in. Some are looking for illegal stuff they can’t buy elsewhere, like drugs or counterfeit documents.
2024 has nonetheless been a productive year, as attack volume was relatively sustained and some ransomware groups have still managed to eke out payments — albeit in lower amounts. Below, we’ll take a closer look at three key trends that defined crypto crime in 2024 and will be important to watch going forward. Fraudsters in possession of a hacked PayPal account can also try to double their money by using the account funds to run various well-established chargeback scams on merchants who accept PayPal. Log-ins for everyday services like Netflix and Spotify primarily offer a route into potential identity theft, since it remains so common for people to reuse their passwords.
#BHUSA: Microsoft Debuts AI Agent Able To Reverse Engineer Malware
By gaining one set of valid credentials, hackers use software to automate checking that log-in against thousands of other online services. The results will either be used for identity theft or sold on the dark web for a profit. Where possible, remove your personal information from any websites that don’t require it.



