The dark web is not meant for the general public since it is harder to access and need technical knowledge. The dark web, sometimes called the black web, is the part of the internet that isn’t indexed by standard search engines and requires a special browser to access. It’s notorious for illegal activity, but many people use it just to browse anonymously. Learn more about what the dark web looks like, then get a VPN to stay more private when you browse the web.
Safely Browse And Verify Onion Sites
While you can visit the obscure part of the internet without a VPN, it’s better to go with one. Here are our favorite choices that work well and support Tor Over VPN perfectly. If you don’t know where to start, you can use The Hidden Wiki to find a few dark web domains. Simply copy the URL of the site you want to visit, press Enter, and you’re all set.
How To Find New, Active Dark Web Links
- The child pornography site Playpen is one of the famous scenarios that resulted from the dark web.
- Examples of the deep web include any websites that are behind a paywall or require login credentials.
- From there, it will go through a VPN server that conceals your IP and wipes geo-locations tags and other elements your Government or ISP might use to track the request.
- In short, even with Tor, there’s no perfect anonymity online, but there are efforts to claw back our power online, says Lewis.
- Like NordVPN, this provider doesn’t store logs and has around 20 third-party audits to prove it.
When you use Tor, which routes your internet traffic through many different relay nodes, your online activity is obscured because you’re browsing anonymously. Tor is a web browser that lets you stay anonymous online or access the dark web. Tor shares similarities with VPNs and proxy servers — all of these tools allow anonymous browsing. Tor can be used together with a VPN to provide overlapping layers of privacy and anonymity.
How To Get On The Dark Web: A Step-by-Step Guide

The Tor browser provides access to “.onion” websites, which are Tor hidden services that you can only access through the Tor browser. You can access these websites without worrying about someone snooping on a Tor exit node, offering more private browsing of what is known as the deep web. Accessing it without proper protection exposes you to surveillance, tracking, and potential security risks.
Step 2: Download Tor Browser
For example, China uses the Great Firewall to block access to Western sites. Accessing blocked content can result in being placed on a watch list or imprisonment. Law enforcers can use custom software to infiltrate the dark web and analyze activities. You could be monitored closely even if you are not doing anything illegal. Activists and government critics prefer to remain anonymous, fearing repercussions if their identities are revealed. Besides, victims of crime may want to hide their identities from their perpetrators.
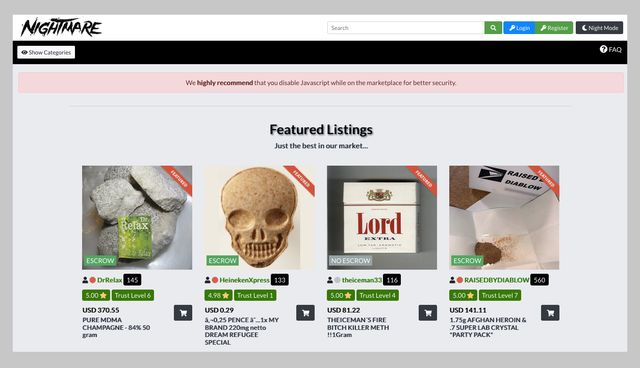
Dark Web Marketplaces
Connecting to the Tor network might raise eyebrows depending on who and where you are. Although data sent through Tor can’t be tracked or decrypted, your internet service provider and network administrator can still see that you’re using Tor. The VPN’s encryption will hide from your ISP the fact that you’re using Tor. Unlike Tor, however, it cannot be used to access the public internet. It can only be used to access hidden services specific to the I2P network. I2P cannot be used to access .onion sites because it is a completely separate network from Tor.
Drug Trafficking Sites
This makes it slower than a VPN and also very difficult to try and get a new IP address in a specific country, which is easy to do with a VPN. Because the Tor network is run by volunteers, there’s also little in the way of accountability. Bad actors can compromise nodes, with exit nodes being of particular concern.
First, you need a web browser that’s capable of utilizing the Tor protocol. That means that if your incoming traffic is routed through a node operated by cybercriminals, they can inject malware into the code of the response, without you ever knowing that it’s happened. The terms “deep web” and “dark web” are commonly used interchangeably.
Tor Vs Alternative Solutions: What’s Best For You?
You can also take a look at the blogs & essays section if you want to find some nifty coding resources. At first glance, Tor doesn’t look that different from your regular browser – it has a search bar, lots of quick-launch icons, the peeled onion icon smack in the middle of the screen. I strongly recommend surfing on the dark web using virtual machine software instead of your locally installed Windows.
Best Practices For Safe Tor Usage:
- Instead, you need a specific configuration, software, or authorization, such as Tor, to access it.
- Tails is a mere 1.3 GB download, so on most connections it will download quickly.
- The problem with the dark web is that, despite legal use, it also remains a hub of illicit activity.
- Other sites explicitly block search engines from identifying them.
Note that most dark web transactions are carried out using Bitcoin or other cryptocurrencies. The dark web is part of the internet that is not indexed by standard search engines like Google, Yahoo, and Bing. It means you cannot access websites on the dark web with regular browsers like Firefox or Chrome. Instead, you need a specific configuration, software, or authorization, such as Tor, to access it. Unlike other search engines, it does not collect or share web activities and personal data of users. Stolen information from data breaches, drugs, guns, malware and various other illegal items can be bought there.

Go to the directory where you saved the downloaded Tor Browser installation file. Choose your language and click “OK.” Follow the installation prompts. The browser is available for Linux, macOS, and Windows desktop and laptop computers. A Tor Browser from the Tor Project is available for Android, and The Onion Browser from developer and journalist Mike Tigas is available for iOS mobile devices, which the Tor Project links to. The Tor Browser is a modified version of the Mozilla Firefox browser and includes the TorButton, TorLauncher, NoScript, and HTTPS Everywhere Firefox extensions, along with the Tor proxy.
Popular Posts
Yes, governments and law enforcement agencies have developed sophisticated techniques to track and investigate illegal activities on the dark web. They can sometimes identify users through other methods, such as monitoring behavior, exploiting vulnerabilities or conducting undercover operations. It’s simply a part of the internet designed to offer anonymity and privacy. While it does host illegal activities and shady content, it also supports legitimate uses like secure communication for activists, journalists, and whistleblowers in oppressive regimes. The dark web itself is neutral; how people use it is what makes it good or bad. A VPN encrypts your internet connection and masks your IP address, making it difficult for anyone to trace your online activities back to you.



