Companies use dark web monitoring to scan for leaked data, stolen credentials and breach indicators, helping them track and identify perpetrators. But let’s be realistic, the best defence isn’t just playing detective after the fact. It’s making sure your sensitive information never lands there in the first place. Freelancing alongside these roles, his work has appeared in publications such as Vice, Metro, Tablet and New Internationalist, as well as The Week’s online edition.

Ross Ulbricht, the creator of Silk Road, was arrested on suspicion of hiring a hitman to kill six people, but the charges were later dropped. People can contact assassins on the dark web who are ready to kill for money. This is an estimated reading time to let you know how long it will take you to read all the content on this particular PrivacySavvy.com page.
Regulatory Measures And Legal Reforms
The urban legend of ‘Red Rooms’ that features live murders has been debunked as a hoax. Some websites monitor and analyze the dark web for threat intelligence. Interestingly, darknet sites also offer stolen documents and passports from around the globe.
Step-by-Step Guide To Accessing The Dark Web Safely With Tor (
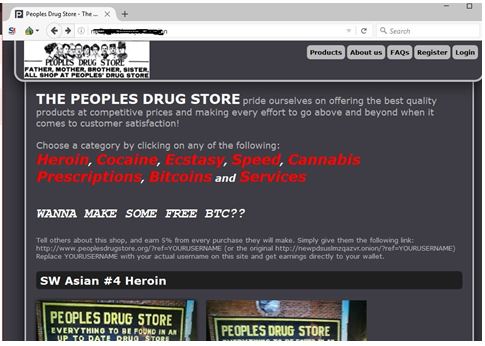
Tails is a mere 1.3 GB download, so on most connections it will download quickly. You can install it on any USB stick that has at least 8 GB of space. You can either sell or buy goods on the dark web, but both present difficulties. These high levels of anonymity increase the opportunity for the “bad guys” to sell drugs, stolen IDs, credit cards, weapons, and many more compromised products or information.
Recommended Dark Web Search Engines And Directories
- These computers are all owned by volunteers, passionate about privacy and happy to offer up their device to help others.
- Scammers prowl the dark net, launching fake storefronts that vanish overnight, often with their victims’ money.
- The Tor Browser is automatically configured to provide a certain level of privacy and security.
- This guide provides clear, step-by-step instructions to safely explore the Dark Web using Tor, helping you stay protected, informed, and anonymous.
As an average Internet user, you may accidentally stumble upon such content. Your access to illegal content, even if it is unintentional, can violate laws in many countries. The dark internet is designed to provide anonymity by keeping communication private through encryption and routing online content through multiple web servers.

Step 6: Access The Tor Browser On Tails OS
By following these tips, individuals can enhance their safety and privacy while exploring the Dark Web. The dark web operates on specialized networks that require unique software to access, such as Tor (The Onion Router). This technology routes user traffic through multiple encrypted layers and relays across the globe, obscuring the user’s IP address and location. There are various sites on the dark web dedicated to the distribution and discussion of hacking tools, cyberattack services (such as DDoS attacks), and information on data breaches and leaks. These sites can be used by both hackers and individuals looking to exploit vulnerabilities.
What Cybersecurity Surprises Does 2018 Hold?
That effort was never fully realized, but the US military published the code under a free license in 2004. Researchers from the Electronic Frontier Foundation and other groups continued its development and launched the Tor project in 2006 as a tool for journalists, activists, and whistleblowers. A VPN allows a user to encrypt all internet traffic traveling to and from his or her device and route it through a server in a location of that user’s choosing. A VPN, in combination with Tor, further enhances the user’s security and anonymity.
Don’t Buy Anything
Not only do you need a dark web browser, you need a dark web search engine too. This search engine will get you to the sites you need, though you can also go directly to dark web addresses if you know what they are, as with standard URLs. Tor is like the public-facing door to the dark web, and there are even mobile apps for Android and iOS. As I’ve mentioned, the dark web isn’t just a place of eternal torment, teeming with drug dealers, human traffickers, and a hitman.
- Look for reputable forums or communities where users share their experiences and recommendations.
- Other porn-related content found on the dark web includes revenge porn and sexualized torture, and the killing of animals.
- Your internet activity is still subject to exit node risks, so always use HTTPS and avoid entering any personal information on unencrypted sites.
- These marketplaces resemble the familiar online black markets but operate within the Dark Web’s encrypted environment.
- We are independently owned and the opinions expressed here are our own.
Scammers prowl the dark net, launching fake storefronts that vanish overnight, often with their victims’ money. In 2017, a global police operation brought down AlphaBay, the dark web’s largest illegal marketplace, shaking the underground economy. To access the Dark Web, you have to use a browser called Tor, also known as The Onion Router. This is the only way to ensure a maximally anonymous – as well as safe – browsing experience on the Dark Web. With dangers like this in mind, it’s even more important to stay safe when surfing the Dark Web than any other part of the internet.

The best way to protect yourself from Dark Web dangers is to avoid involvement with it altogether. Unless you have an explicit and legitimate reason to access the Dark Web, it is advisable to stay away from this hidden realm. Engaging in illegal activities or exploring illicit marketplaces on the Dark Web puts you at risk of legal consequences and exposure to dangerous elements within the anonymous network.
Let’s take a closer look at the best VPNs you can use to safely access the dark web. Then, a law enforcement agency (still unidentified) provided information to the FBI that later accessed the site’s host server. Removing your sensitive personal information from the dark web once it has been exposed is virtually impossible.
This type of government surveillance applies mostly to countries with environments that are hostile to free speech. That alone might already raise suspicion and place you under special surveillance. Some reports say the FBI will simply label you a “criminal” once they’re aware you’re using the Tor browser.
Therefore, it’s best to use a VPN no matter the personal device you’re using. Traditional social media platforms such as Facebook have also created versions that work with the dark web to provide services across all dimensions of the World Wide Web. However, unlike Facebook, the DWSN requires users to remain anonymous and not reveal personal information to protect their privacy. The dark web is a hidden part of the internet that requires a special browser like the Tor browser to access it. Normal search engines like Google and DuckDuckGo don’t index this part of the web due to its illegal nature.



