
The dark web is often confused with the deep web, but they are different. The deep web includes everyday online services requiring authentication (e.g., banking portals, medical records), while the dark web hosts anonymous websites. Merely downloading, installing and using the Tor Browser is not illegal.
Accessing On IPhone (iOS)
However, not all the forums and social media sites are legal on the dark web and often include shocking conversations and pin boards by anonymous users. This is below the surface web and accounts for about 90% of all websites. This portion includes academic journals, private databases, and other content hidden from the public for various reasons. The dark web is a hidden part of the web that is not indexed by traditional search engines like Google and requires specialized software to access. Tor over VPN requires you to place some trust in your VPN provider but not your ISP, and is best if you want to access .onion websites. VPN over Tor requires you to place trust in your ISP but not your VPN and is best if you want to avoid bad Tor exit nodes.
- No longer restricted to dial-up, many of us now consider access to a stable high-speed internet connection a critical element of our daily lives.
- The most common of these browsers is Tor, which launched in 2002 and serves millions of users.
- It has a range of settings you can configure to help with security and privacy.
- These laws should cover what you need to know about using a VPN, proxy server, or Tor Browser to connect to the internet.
- The difference between the dark web and the deep web is that the deep web refers to websites and web pages that aren’t indexed by search engines, like login pages and payment portals.
- Get Avast BreachGuard for Mac to protect your privacy and keep your personal data from falling into the wrong hands.
All Surfshark servers are RAM-only and support the WireGuard, IKEv2, and OpenVPN protocols. The company operates a strict no-logs policy and protects internet traffic using AES-256-GCM encryption together with a SHA512 authentication hash and 2048-bit DHE-RSA key exchange. While NordVPN is undoubtedly a great service, it’s not without fault.
onion URL Structure
In case of an attack, you can be sure that any of the data or information stored on your main computer will be safe. But remember, it’s essential to take all the necessary and important security steps before entering such sites on the dark web. As mentioned before, your ISP and government institutions are not able to see what sites you visit on the Tor network, but they can probably see that you use Tor. However, there are several “.onion” search engines like “onion.city”, “onion.to”, and “notevil” that you can use to find suitable marketplaces. Data gleaned from ransomware and data breaches is available on the dark web. Millions of customers’ personal data, including names, addresses, bank account and credit card account information, and many other forms of sensitive data.
Use Cryptocurrency Safely
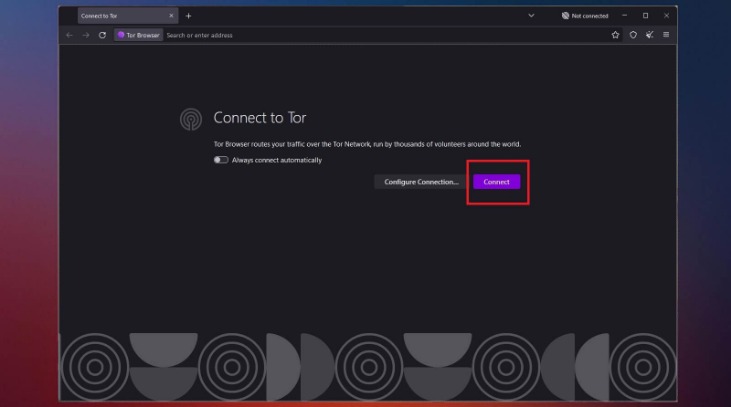
It tends to conjure vague notions of bad people secretly doing bad things. But while it certainly is a place where illegal activities are facilitated, it can also be a force for good. For one, the VPN can’t see your online activities because of VPN encryption. Plus, the ISP won’t see that you’re using Tor, which is excellent.
Roundup – Best VPNs For Speed
For example, DuckDuckGo is the most popular but often shows repetitive results and is sometimes unrelated to the question. The Camouflage Mode is intended for people living in countries with heavy internet censorship, like China. It will make your VPN activities seem like normal traffic, so you can use an uncensored internet.
Find The onion Address You Want To Access
The anonymity provided by onion routing comes at the cost of slowing your internet considerably. As such, we do not recommend using Tor if you want to do data-intensive activities like streaming in HD, gaming, torrenting, or making video calls. Many reputable websites and news outlets like ProPublica and SecureDrop often share official domain addresses of onion sites on their pages.
Our Network
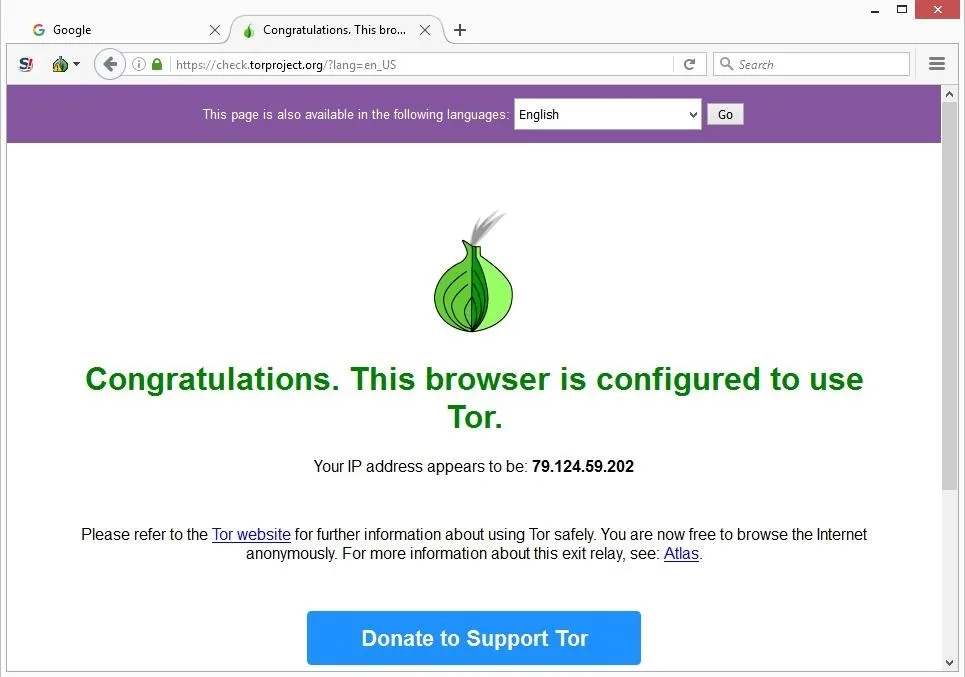
To conduct this check, just turn on your VPN and head over to ipleak.net and dnsleaktest.com to see if the IP address displayed is the one from your VPN. These efforts could very well include accessing the dark web to help victims and hunt down criminals. This process, though, can often involve accessing the dark web for research into the most current malware on the market. That being said, the anonymity offered by the dark web is the perfect breeding ground for criminals from all walks of life and users are advised to browse with extreme caution. Again, it’s DOT Security’s advice to stay off the dark web entirely.
WANT TO TRY THE TOP VPN RISK FREE?
With rising online privacy concerns in the current digital age, the Tor network’s anonymity is becoming essential. It is a good way to prevent third parties from tracking online activities. People in countries with heavy internet censorship must get a VPN or Tor browser to access the surface web.
What Percentage Of The Internet Is Dark Web?

Did you know that a stolen laptop costs businesses an average of $49,000 in lost data and productivi… Yes, via apps like Tor Browser for Android or Onion Browser for iOS, but desktops offer more security. A piece of tape over your webcam essentially prevents any possible remote activation by malware. Assume that everyone and every site is trying to take advantage of you. Avoid giving up real information, don’t log into your personal accounts, and don’t engage in conversations that could identify you.
Plan Ahead Before Connecting
Well-known news websites, such as ProPublica, have launched deep websites. Meanwhile, Facebook also offers dark web access to their social network. NordVPN offers a 30-day, no-risk trial subscription when you sign up on this page. This provides a full month’s access to all of the features of the #1 VPN for the Dark Web.

Each of these options offers unique privacy features, with Whonix and Qubes for higher security setups, and Kodachi and Liberté for portability. Choose a VPN known for strong encryption, a no-logs policy, and compatibility with various devices. Ever found yourself urgently needing to adjust your network, security, or user preferences—only to… Yes, many organizations monitor the dark web for cybersecurity intelligence—always in line with legal compliance.



