Accessing the dark web using equipment like the Tor browser doesn’t fall under criminal activity. Engaging in illegal activities like buying stolen records, drugs, or weapons—can get you into a criminal problem. This means that even just looking around on the dark web can be risky if you’re not cautious. For example, downloading files could infect your computer with malware. Paying for illegal services or products can leave you vulnerable to scams or draw the attention of law enforcement. Joining suspicious forums might connect you with criminals or put you on the radar of investigators.
Find The onion Address You Want To Access
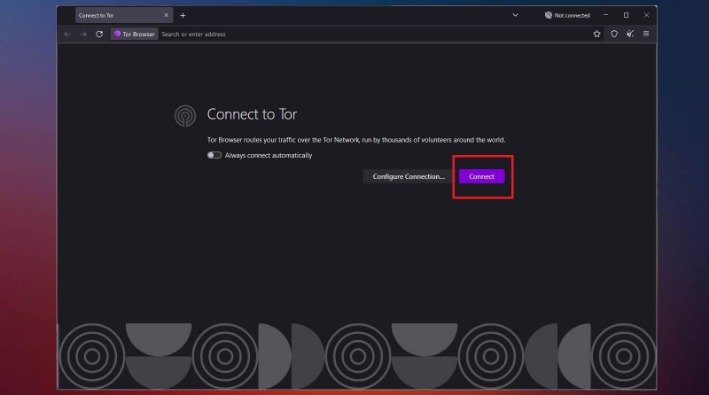
If you’re just browsing the dark web out of curiosity, Tor, or a Tor and VPN configuration is safe enough. If you’re trying to hide from an oppressive government or want to be a whistle-blower for something illegal, take as many steps as you can to be safe. H25.io is a premium directory in the Tor network, offering access to a diverse and meticulously curated list of onion sites. Our mission is to simplify navigation in the complex and evolving world of the darknet. Here, you’ll find links to various resources, including educational archives, private forums, anonymous services, and more. Before you embark on your journey into the Dark Web, it’s crucial to establish a secure foundation.

Accessing the Dark Web requires cautious navigation, and adhering to certain tips can help ensure a safer and more secure experience. Use VPN, avoid logging into personal accounts, enable Tor security settings, and stick to trusted sites. Secure communication for journalists, accessing privacy-focused forums, and whistleblower submissions.
Which Browser Do I Need To Access The Dark Web On My Phone?
This allows you to use the computer without the risk of corrupting your computer’s normal operating system with viruses or malware. Tails also protects you from possible malware, viruses, or keystroke loggers that may have already infected the computer, as it doesn’t run the operating system already installed on the device. Keep in mind what you’re looking for, find that information, and disconnect from the dark web. As enticing as it might be, don’t follow links to other parts of the dark web. Check around with other users and ask if they know anything about the new marketplace. Unfortunately, it’s also a place where the bad guys can offer their services – for example, hackers or hitmen.
Hacking And Cybercrime Tools
Cloudwards.net may earn a small commission from some purchases made through our site. PCMag has a guide for staying anonymous as you navigate the clear web. I don’t recommend seeking out dark web content unless you have a specific reason to do so.
Identity & Data Protection
Journalists, whistleblowers, and researchers often use it to protect their privacy or gather sensitive information. While Tor browsers are used to access the dark web, search engines play a crucial role in facilitating the browsing experience for users. Since Google and surface-level search engines don’t work in the dark web world, users often opt for these search engines that enhance their experience and accessibility on the platform.
Special Feature

Not to mention that anonymity safeguards won’t protect you from other threats like hacking and malware. There are media websites on the dark web—both legitimate and illegitimate—that allow users to access digital media outside the highly monitored surface web. As you might expect, these websites sometimes host explicit, gory, harmful, and illegal content. Yes, your ISP can see if you access the dark web, but not what you do on it.
The place is as messy and chaotic as you would expect when everyone is anonymous, and a substantial minority are out to scam others. The dark web is a subset of the deep web that is intentionally hidden, requiring a specific browser—Tor—to access, as explained below. No one really knows the size of the dark web, but most estimates put it at around 5% of the total internet. Again, not all the dark web is used for illicit purposes despite its ominous-sounding name.

While there are some threats on the surface web, and users need to browse with some level of security awareness, it’s a lot easier to stay safe on the surface web than the dark web. There are a lot of dangers lurking in the corners of the dark web as it’s a well trafficked playground for cybercriminals and is riddled with criminal markets that span the imagination. The VPN will protect your traffic when you connect with military-grade AES 256-bit encryption. This is high-level protection; no one can intercept your data or activities.
- Generally, it’s important to use Tor responsibly and in accordance with local laws and regulations.
- You might be used to typing in a word or phrase on the surface web, hitting “Enter,” and receiving pages of results.
- While no method guarantees complete anonymity, you can minimize the chances of being tracked with the right precautions.
- For added protection, it’s best to use a VPN like ExpressVPN to encrypt your internet traffic and mask your IP address while establishing the initial Tor connection.
- The dark web has flourished thanks to bitcoin, the crypto-currency that enables two parties to conduct a trusted transaction without knowing each other’s identity.
Can Tor Browser Be Used For Regular Internet Browsing?
For example, DuckDuckGo is the most popular but often shows repetitive results and is sometimes unrelated to the question. The Camouflage Mode is intended for people living in countries with heavy internet censorship, like China. It will make your VPN activities seem like normal traffic, so you can use an uncensored internet. However, this feature is only available on iOS, Android, and Windows. Since Tor has to pass your traffic through several nodes, it will slightly slow your speeds.
Can Cybersecurity Teams Use The Dark Web To Track Threats?
Its strongest appeal is that it has strong privacy defaults, making it usable for daily use that can be expanded upon. It is perhaps the most secure way to run applications anonymously. If you want a strong setup that has no leaks, Whonix might be the best dark web browser solution on the market. Purchases through links on our pages may yield affiliate revenue for us.
Watch Out; Your ISP Could See You Using The Tor
Some websites monitor and analyze the dark web for threat intelligence. The story hints at why taking dark web safety measures is essential, even if you are jumping into the dark side of the internet only because of some curiosity. The information can be of any kind, either social security numbers or even bank card numbers (the bank/credit card information is usually sold in bulk). Due to its hidden nature, the dark web is also famous for the names underground internet and black web. However, don’t fret yourself about this frightening concept, than the actual meaning of the dark web.

No node can track the complete path the traffic has taken, and more importantly, neither can anyone who finds it on the other side. Only the entry node can view your IP address (more on how to stop this happening later). For businesses and individuals alike, the Dark Web poses unique threats that go beyond individual use. From data breaches to counterfeit products and unauthorized brand use, malicious actors exploit the Dark Web’s anonymity for financial and reputational harm. ZeroNet is a decentralized, peer-to-peer network that allows users to create and host websites without the need for a centralized server. It provides anonymity and censorship resistance and is available for Windows, Mac, and Linux.



